Security researchers have discovered a new strain of ransomware that encrypts users files and redirects users to an online page to pay the ransom via credit/debit card.
The ransomware is not under active distribution and appears to be still under development. First samples were spotted by security researcher MalwareHunter going back to January 15.
The ransomware identifies itself as MindLost, but Microsoft detects it as Paggalangrypt.
The ransomware works and does encrypt files. It targets a small number of file extensions but will search files on all the storage devices, with the exception of folders containing the strings:
Program Files
Program Files (x86)
The biggest clue that MindLost is still under development, is that this filter is not active yet. Searching and encrypting files on all the storage mediums is time consuming, so current MindLost samples bypass this behavior and only encrypt files in the "C:\\Users" folder. Stable versions will likely not feature this filter.
The file types it targets are:
.jpg
.mp3
.mp4
.png
.py
.txt
All encrypted files will receive a new extension .enc, such as a file named image.png will become image.png.enc.
Once the encryption ends, the MindLost ransomware will download an image from the below URL and set it as the computer's new desktop wallpaper. This image contains instructions for recovering files.
http://image.ibb[.]co/kO6xZ6/insane_uriel_by_urielstock_4.jpg

For persistence, MindLost also sets a registry key to ensure its executable is started after every reboot.
HKU\Administrator\Software\Microsoft\Windows\CurrentVersion\Run
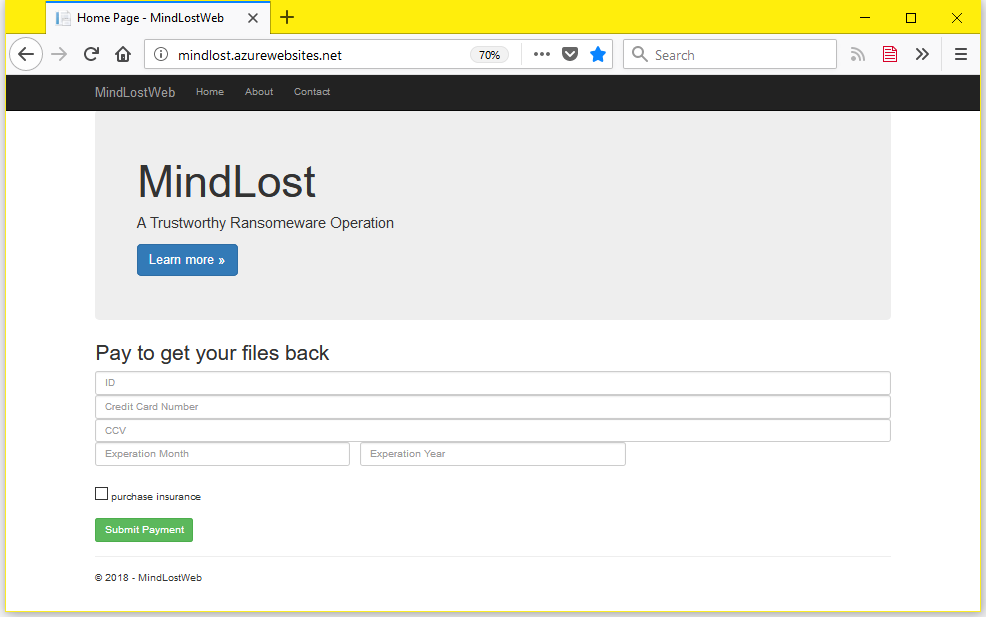
The ransom note instructs users to visit the following URL to buy a decrypter app that will decrypt files.
http://mindlost.azurewebsites[.]net
|
|
|
Shady ransom payment system
What is incredibly strange is that MindLost does not ask for payment via Bitcoin, but via credit/debit card. There are a few things wrong here.
First, to process any transaction, the MindLost author would have to register as a merchant and give up a wealth of information about himself, something that we don't believe he intends.
Second, the author may be using the ransomware just to trick victims into entering payment card details on his site, which he may later abuse for various fraudulent operations, or sell them to other hackers.
Or third, the credit/debit card payment system may be a template on an unfinished website, which the author may replace in the future.
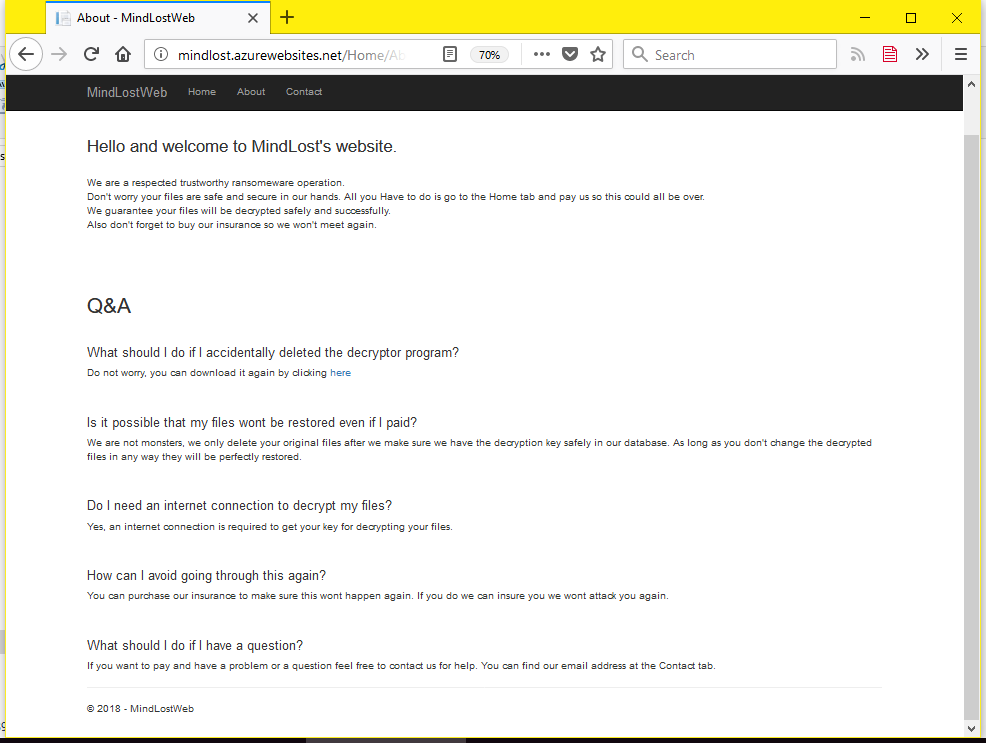
The other thing that also stood out was MindLost's "insurance" option, which is supposed to safeguard a computer from getting reinfected with the ransomware again. This is the second time we've seen a "reinfection tax" advertised by a ransomware strain. We've seen it before with Spora, where it was called "immunity."
MindLost has poor OpSec
Overall, the entire ransomware is garbage, compared to other more well-put together strains recently released.
For example, the ransomware's binary contains file paths that include a man's name (Hi Daniel Ohayon!). While this could be a false flag meant to make researchers follow wrong leads, it is not the only mistake.
The ransomware binary also comes with hardcoded credentials for MindLost's remote database. Shipping hardcoded database credentials in a binary is as bad as it gets when it comes to good programming practices. In addition, it's an OpSec epic fail, as any security researcher analyzing the ransomware can connect to this database and retrieve victim data, such as encryption/decryption keys.
According to MalwareHunter, there have been only four samples of the MindLost ransomware detected on VirusTotal, and most look like in-dev versions, which is a good thing since the ransomware author can still give up his foolish effort and stop all development.
If this ransomware enters active distribution, victims should be wary of inputting payment card details in the ransom payment form, as it could also lead to mysterious transactions appearing on card statements later down the road.
File hash: 6d874c9aa367238b39176467cb1677366a2735a2dfbcce4ff69ebd67ed3ab529


Comments
granada12 - 6 years ago
"Respected trushworthy ransomware operation"
Of course! We just stole your file and we want your money if you want to get it back but don't worry we are a respected trushworthy ransomware operation.
I feel much better knowing that now. ('sarcasm') haha :)