
A string of weaponized attacks targeting Adobe's Flash media player—including three in the past 10 days—has kept software engineers scrambling to fix the underlying vulnerabilities that make the exploits so dangerous. Fortunately, they have also been busy making structural changes to the way the program interacts with computer operating systems to significantly reduce the damage that can result not only from those specific attacks but entire classes of similar ones.
At the moment, the defenses are fully implemented only in the Flash version included in Google Chrome, having made their debut earlier this week. One of the two mitigations is available in other versions of Flash, and the remaining one is expected to be added to other browsers in August. Had they been widely available earlier, they likely would have blunted the effects of at least some of the three most recent zero-day vulnerabilities, which were leaked following the thorough hack of Hacking Team, the malware-as-a-service provider that catered to governments around the world. To block entire classes of new exploits, Adobe engineers, with the help of their counterparts at Google's Project Zero team, have made two key changes, which were documented in a blog post published Thursday.
The first, which is currently available only in Chrome, is a new partition added to the heap, which is a large pool of computer memory. The partition isolates different types of memory contents, typically known as objects, from each other so one can't be used to hijack or otherwise tamper with another. Heap partitioning has long been a mainstay in Chrome and other browsers. Now it's a key defense in Flash.
Had heap partitioning been a part of Flash earlier, it would have significantly complicated some of the exploits that recently came to light in the Hacking Team breach. That's because the exploits modified the "Vector." object after a portion of heap where it had resided was freed. The tampering allowed the attackers to inject malicious code into computer memory and from there install their malicious software on the underlying computer. Similar Vector. tampering was also a part of separate, in-the-wild exploits from earlier this year. According to Project Zero team members Mark Brand and Chris Evans, the exploits looked something like this:
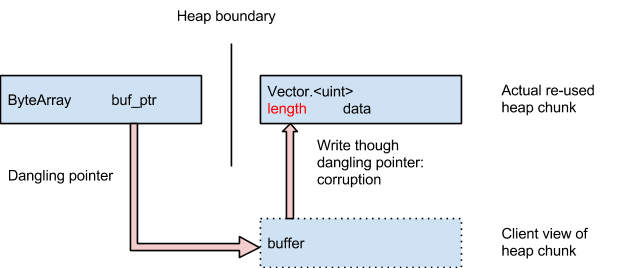
Under the new Flash design, an unmapped space forming a no-man's land of sorts is put between the Flash heap and the system heap, making it significantly harder for exploit code to access the Vector. object. Not only does it help defend against use-after-free classes of attacks, it also makes it harder to carry out buffer-overflow exploits.
"We have now defended the integrity of Vector buffers from both heap overflow and use-after-free attacks!" the Project Zero researchers wrote. "In the case of a heap overflow within the Flash heap, the Vector buffer objects are simply not there to corrupt. In the case of the use-after-free, when the attacker tries to allocate the Vector. buffer to occupy the free heap chunk of interest, it will not end up being allocated there because it lives in a different heap."
Under the new design, a buffer overflow attack might look like this:

Got 64 bits?
To get the full benefit of this new defense in Chrome, Windows users with 64-bit systems should make sure they're using the 64-bit version of the browser. That's because the significantly higher number of memory addresses, as compared with the 32-bit version, makes heap spraying and other common exploitation techniques much harder. People using a 64-bit version of Windows should enter chrome://chrome into their address bar. Unless a string with "64-bit" appears in the resulting window, the version is 32 bits. If that's the case, it's worth uninstalling the browser and replacing it with a 64-bit version of Chrome.
Besides heap partitioning, Adobe has added a second mitigation. It comes in the form of a validation secret that attack code must have access to before making changes to Vector objects. The additional measure helps protect users of 32-bit browsers and is also a good example of what security researchers call defense in depth. True to that philosophy, the Project Zero engineers said they're working on additional defenses, including browser sandboxes and compiler-based mitigations.
"It's a cat-and-mouse-game, but we'll be looking out for attackers' attempts to adapt, and devising further mitigations based on what we see," they wrote. "Perhaps more importantly, we're also devising a next level of defenses based on what we expect we might see. Our partitioning mitigation is far from finished. We’ll be analyzing object types to see what else might benefit from partitioning, and moving forward incrementally."
reader comments
94