
SAN FRANCISCO — The first tweets appeared on April 14. The website of Al Hayat, a pro-Saudi newspaper, had been hacked, its front page replaced to threaten Saudi Arabia against getting involved in Yemen’s growing civil unrest. A group calling itself the Yemen Cyber Army took credit for the hack. Few took notice — amid the breaches of government databases and hacking armies with groups claiming affiliation with groups like ISIS, the takedown of a newspaper website was hardly news.
But the campaign continued to build. Twitter accounts were created calling for hackers to attack Saudi targets rallying around the hashtag #OpSaudi. On May 20, the Saudi foreign ministry was hacked. The next day, a story appeared on Iran’s state-run FARS news agency, the first media mention of the group (followed quickly by a second press mention on Russia Today). The FARS story credited the Yemen Cyber Army with carrying out the hack of the Saudi foreign ministry and said it would soon be releasing personal information about Saudi federal employees as well as diplomatic correspondence. In the week that followed, documents surfaced in Pastebin accounts with passport information that appeared to come from the Saudi foreign ministry.
Fast forward to one month later, when Wikileaks announced it would make public roughly one million diplomatic cables from Saudi Arabia’s foreign ministry. Wikileaks’ press release mentions that “a group calling itself the Yemen Cyber Army was responsible for breaching the Saudi Foreign Ministry,” but stops short of naming the group as the source of the documents being uploaded to Wikileaks. The documents range from cables outlining Saudi Arabia’s funding of Islamist groups in the region, to a request from Osama bin Laden’s son for his father’s death certificate. It was the first news-making event for Wikileaks since November 2013.
Who is the shadowy group that appears to have launched a full-scale digital campaign to expose, or at least embarrass, Saudi Arabia?
Like many hacking outfits, the Yemen Cyber Army has no spokesperson and releases few details. By its name, we are led to assume it’s based in Yemen — currently caught in a bloody proxy war between Saudi Arabia and Iran — but there is no proof. In conversations with BuzzFeed News and other news outlets in mid-May, individuals who associate themselves with the Yemen Cyber Army have claimed that they are in Yemen, though they refuse to speak Arabic or answer details about their location. Since Wikileaks began publishing the trove of diplomatic cables, they have gone dark, refusing to answer questions from journalists about how they came to work with Julian Assange.
Now, cybersecurity experts are digging in to try to figure out who was behind the massive breach of the Saudi foreign ministry and what type of further threat the group could pose to the region’s most secretive and wealthy government.
Boaz Dolev, head of ClearSky, an Israeli cybersecurity company that has studied the malware behind cyberattacks across the region, is convinced that the Iranian government is behind the group.
“Anyone who thinks a group of hackers from Yemen managed to hack into Saudi Arabia is delusional, or doesn’t understand anything about the world of hacking today,” he said by telephone from Israel. “Why would Iran want to put their name on this? Why would they claim responsibility when it is easier, cleaner, to throw the blame on another country?” he said.
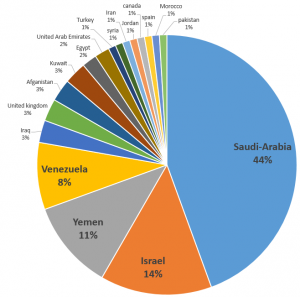
ClearSky has identified a piece of malware that has been deployed against more than 550 targets — nearly half of them in Saudi Arabia, another 14% in Israel and 11% in Yemen.
“We estimate that this access is used for espionage or other nation-state interests, and not for monetary gain or hacktivism,” Dolev wrote in a recently released report. “Various characteristics of the attacks and their targets bring us to the conclusion that the threat actors are Iranian,” he wrote. “The attackers speak and write in native Iranian Persian and make mistakes characteristic of Persian speakers. In one of the hacked accounts, when retrieved, the interface language had been changed to Persian.”
Dolev added that several of the IP addresses were traced back to locations in Iran. While his evidence seems strong, in the games of smoke and mirrors that get played in cyberespionage, countries can insert deceiving language or fake IP addresses to try to scapegoat another country. What seems certain, Dolev said, was that a nation-state was behind what he called “sophisticated and aggressive malware.” He said the attacks followed a pattern: First a targeted “spear-phishing” email designed to gain the trust of the target would be sent loaded with the malware that his firm has been tracking; then if that didn’t work more sophisticated follow-up attacks, ranging from false Gmail logins to YouTube pages, would be sent in an effort to access the target’s systems and install the malware.
Once installed, the malware entered the target's system, then gained access to the targets’ emails, documents, and other forms of communication, which the malware’s creator could then remotely access and copy. The ClearSky report concluded that it appeared to be built for espionage, as the malware exists in a computer without overtly malicious side effects and does not destroy the data it accesses.
The malware, which ClearSky calls Gholee, has other names among other cybersecurity companies, several of which likewise found links between it and Iran. The Tokyo-based cybersecurity company TrendMicro, found the malware in an Iranian-linked campaign they call Operation Woolen-Goldfish. The U.S.-based FireEye cybersecurity firm has connected the malware to a group they call the Ajax Security team, which they also conclude is based in Iran.
ClearSky, TrendMicro, and FireEye all concluded that it was likely the Iranian government behind the malware, rather than individuals in Iran, due to the resources and amount of time it would take to develop. Though Iran is hardly public about its cyberwarfare capabilities, researchers don’t believe Iran has the same type of organized pseudo-governmental hacking collectives that exist in China and Russia. In August 2012, when malware struck Saudi Aramco, the NSA concluded that the Iranian government was behind the malware, nicknamed Shamoon. They had created it, according to one NSA document, by mimicking a piece of malware (likely U.S.- or Israel-made) that years earlier had attacked and wiped clean computers in Iran’s oil ministry.
Dolev said that without looking through the computers at Saudi Arabia’s foreign ministry for evidence of Gholee in their systems, it was impossible to say with total certainty that they had been infected by the same malware his company has been tracing.
“I would say I am 90% certain, given the timing and the sophistication of this malware,” he said.
BuzzFeed News repeatedly asked Saudi officials if they could confirm that the malware identified by the cybersecurity companies was the same as that which infected the foreign ministry’s computers. Saudi officials, speaking through the country’s official press agency, said an investigation was ongoing, but refused to comment further. An official who answered the phone in Saudi Arabia’s interior ministry said that “sophisticated malware” had infected computers through a spear-phishing attack, though he declined to be named, saying he was not allowed to speak to journalists.

Other online accounts, which openly expressed solidarity with the Yemen Cyber Army in 2014, began tweeting earlier this year that their movement had been taken over by Iran.
The Twitter users declined to give evidence of Iran’s involvement, but shorly after the tweets appeared they stopped tweeting with hashtags associated with the Yemen Cyber Army. BuzzFeed News reached out to 11 Twitter and Facebook users associated with the group for comment, but was told that at this time they were not interested in speaking to the press.
Wikileaks has refused to comment on the source of the diplomatic cables it released on Friday, though the coinciding with the Yemen Cyber Army hack is hard to ignore.
Wikileaks told BuzzFeed News:
@sheeraf @sunnysingh_nw3 We never comment on sourcing.
The Yemen Cyber Army has made no explicit reference to Wikileaks, but they have pledged allegiance to the hacktivist collective Anonymous, saying in a statement posted alongside their original leak: “Your Network Hacked by Yemen Cyber Army. We Are Anonymous. We Are Everywhere. We Are Legion. We do Not Forgive. We do Not Forget. Stop Attacking Our Country.”
Because Anonymous exists as a nebulous organization, with no central command or anyone able to say a person or group isn’t a member, pledging allegiance to the group can often be used to try to distract from a hacker’s true allegiance.

Since Wikileaks began releasing its cache of cables, Saudi Arabia has shifted from dismissing the leaks as a “minor breach” to, according to some Twitter users, warning its citizens that sharing the cables is a crime punishable by up to 20 years in prison. The leaks, which were originally limited to the passport information of individuals applying for visas to visit Saudi Arabia, have grown into a cache of documents that outlines Saudi Arabia’s resistance to the Iran talks and their advocacy in the West on behalf of GCC countries.
“There is no doubt that this is doing damage to Saudi Arabia’s interests across the region,” said a U.S. diplomat who spoke to BuzzFeed News by phone from Amman, Jordan. He asked to speak without attribution as he was not authorized to speak to the press. “The Arab-language news sites, especially the blogs, have been running with this story for days. Saudi Arabia is so notoriously secretive that even their allies can’t help gushing over cables that tell the inside story of what is going on there.”
The diplomat said he believed the hack was “very successful psychological warfare.”
Abdullah AlAli, chief executive officer of Cyberkov, a Kuwait-based cybersecurity company, told BuzzFeed News that his company has been studying the Yemen Cyber Army for months.
“It is clear that an unannounced cyber war is currently taking place in the Middle East, with no rules of engagement and no official declarations,” he said.
